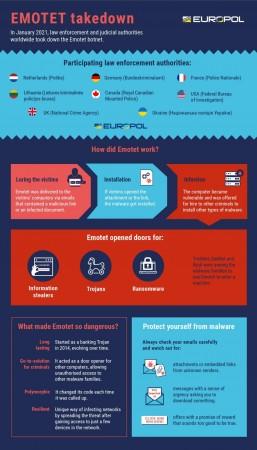
Cybercrimes have evolved into something far more dangerous in these past few years. In what can be declared as a major victory and peace of mind to millions around the world, the world's most dangerous malware botnet was finally taken down after a two-year-long battle. The global forces had joined hands on this one, including the Europol, FBI, UK's National Crime Agency among others.
The sophisticated botnet dubbed as Emotet is touted as one of the most significant ones in the last decade. It first appeared as a banking trojan in 2014 but evolved into one of the most powerful malware in use by cybercriminals. Emotet was used in a number of organized attacks, including manipulation of 2020 US Presidential campaign and infiltrating the world's largest oil company Saudi Aramco. Also, Emotet malware was used to deploy an attack on the Berlin Court of Justice, German individuals and institutions, causing at least EUR 14.5 million in damages.

The deadly malware was capable of stealing passwords, bank data, and even remotely install malicious software for ransomware. The malware would create a backdoor in a Windows PC using phishing emails with an innocent-looking Word document laced with malware. By altering the subject of emails and documents, criminals would lure victims into opening emails, which would install the malware. COVID-19 pandemic was a huge opportunity for these cybercriminals as they would use invoices and notices about the virus to lure victims.
"Emotet was much more than just a malware. What made Emotet so dangerous is that the malware was offered for hire to other cybercriminals to install other types of malware, such as banking Trojans or ransomwares, onto a victim's computer," Europol, the international law-enforcement agency, said in a release.
Taming the beast
The law enforcement agencies from around the world together managed to gain control of Emotet's infrastructure, which comprises of hundreds of servers globally. They did so from the inside - the only way to take down such a massive operation.

"Emotet was our number one threat for a long period and taking this down will have an important impact. Emotet is involved in 30% of malware attacks; a successful takedown will have an important impact on the criminal landscape," Fernando Ruiz, head of operations at Europol's European Cybercrime Centre (EC3) told ZDNet.
The successful takedown was possible with the co-ordination of various global agencies, including Dutch National Police, Germany's Federal Crime Police, France's National Police, the Lithuanian Criminal Police Bureau, the Royal Canadian Mounted Police, the US Federal Bureau of Investigation, the UK's National Crime Agency, and the National Police of Ukraine. But those behind this massive infrastructure remain unidentified, but the quest is on.
What now?
By taking control of the Emotet infrastructure, the law enforcement agencies are going to make sure the cybercriminals won't misuse it. All the machines that have been infected by Emotet are now being redirected to the infrastructure controlled by the law enforcement.
Europol is also working with Computer Emergency Response Teams (CERTs) around the world to identify the systems that have been infected by Emotet. To those who are suspicious of being infected, it is best to use fully updated antivirus software.
Also, do not open emails and attachments from unknown senders. Anyone can check if their email address has been compromised using this online tool.

















