
Security researchers have come across a new variant of the Android.Fakeapp malware that can steal credentials of Uber users, and then use deep links of the original app to hide its wrongdoings.
According to researchers at California-based cybersecurity company Symantec, the newly-discovered malware variant uses a unique monetisation technique, in addition to the common overlay tricks of asking users to enter their credit card details. The malware poses serious threats to Uber users on Android, simply because of the sheer number of people – in the millions – using the app on the platform worldwide.
"Android.Fakeapp is a Trojan horse for Android devices that downloads configuration files to display advertisements and collects information from the compromised device," according to Symantec.
The Fakeapp variant in question uses a spoofed Uber app user interface (UI) which appears on the screen of the affected device at regular intervals until it succeeds to trick users into entering their Uber ID and password.
Once the users click the arrow button (as shown in the image below) to proceed, the malware immediately sends the login credentials to its remote server. What it does next is the most interesting part of the hack the malware performs: covering up the heist.
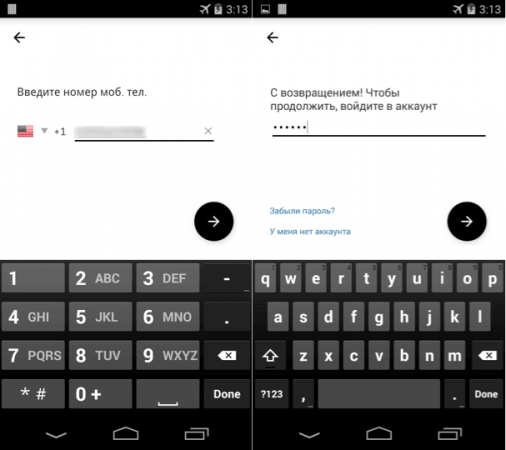
To avoid alarming the victim, the malware displays a screen of the original Uber app showing the user's current location. The Fakeapp variant uses this tactic to minimise the possibility of any suspicion, because showing the user's location details is what's expected of the legitimate app.
But how does the malware make this happen? To show the location screen, it uses the deep link URL of the original Uber app responsible for initiating the app's Ride Request function, with the user's current location preloaded as the pickup point.
"Deep links are URLs that take users directly to specific content in an app. Deep-linking in Android is a way to identify a specific piece of content or functionality inside an app. It is much like a web URL, but for applications," Dinesh Venkatesan, the principal threat analyst engineer at Symantec, said in a blog post.
The best way to stay protected from such mobile threats is to remain vigilant and keep the software up to date. Users should also refrain from downloading apps from unfamiliar third-party websites.
Users should also be aware of the permissions requested by apps, and make frequent backups of important data stored on their devices.









