Security researchers at Symantec have discovered a new Android malware, named "Sockbot", which can allow a remote attacker to use an infected device to generate advertising traffic for the purpose of online ad fraud. The discovery has also led Google to remove eight infected apps from the official Play Store.
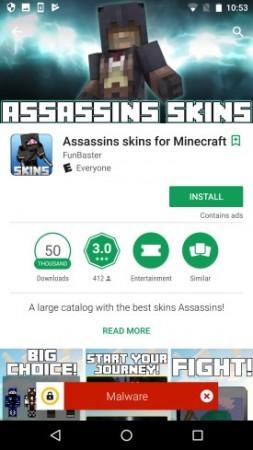
The removed apps, which posed as player skin apps for the Minecraft Pocket Edition mobile game, had been downloaded from 600,000 to 2.6 million times before they were taken down. All the infected apps were developed by the same developer, going by the name of FunBaster.
While the malware's primary targets were apparently the users in the United States, it also had a presence in other countries like Russia, Ukraine, Brazil and Germany.

"Android.Sockbot is a Trojan horse for Android devices that creates a SOCKS proxy on the compromised device," Symantec said on its website. "Once installed, the application will display an icon depicting a ninja character with a blue background and the title of SKINS."
After being installed on a device, the malware requests permissions to perform the following actions:
- Access location information, such as Cell-ID or Wi-Fi
- Access information about networks
- Access information about the Wi-Fi state
- Open network connections
- Read from external storage devices
- Check the phone's current state
- Start once the device has finished booting
- Display alerts
- Make the phone vibrate
- Write to external storage devices
"The legitimate purpose of the apps is to modify the look of the characters in Minecraft: Pocket Edition (PE). In the background, sophisticated and well-disguised attacking functionality is enabled. We set up network analysis of this malware in action and observed activity apparently aimed at generating illegitimate ad revenue," researchers at Symantec said in a blog post.
According to researchers, the infected devices were found to have received ad data such as the ad type and screen size name, but the malicious apps didn't have the functionality to display those ads.
However, the researchers also said that the attacker behind the malware could turn nastier at any point of time and use Sockbot to inject harmful content, or even carry out DDoS attack.
Sockbot Android malware's discovery came more than a month after security researchers took down the WireX botnet, which infected over 120,000 Android devices. Attackers were also using the botnet to launch DDoS attacks.
Here're a few best practices, recommended by Symantec, to stay protected from malicious software:
- Keep your software up to date.
- Refrain from downloading apps from unfamiliar sites.
- Only install apps from trusted sources.
- Pay close attention to the permissions requested by an app.
- Install a suitable mobile security app in order to protect your device and data.
- Make frequent backups of important data.








