
With adult content becoming readily available to people these days, porn sites have turned into a mainstream entertainment source with more audience compared to non-adult sites. Hackers have leveraged this trend to use cyberspace as a tool for their malicious activity, with over one-fourth of all mobile users being targeted in 2017 by porn-themed malware attacks, a report said on Wednesday.
Nearly 1.2 million mobile users encountered malware with adult content to lure victims at least once last year. That is 25.4 percent of all users who encountered any type of Android malware during the year, Russia-based Kaspersky Lab said in the report, adding that its security researchers identified 23 families of mobile malware that use porn content to hide their real functionality.
"Given that the total number of Android malware families we've got in our collection is 1,024, 23 families that are hiding behind adult content is a fairly low number. However, if we look at the scale at which these malicious apps are distributed, things look very different," the security researchers said in a blog post.
According to the report, the types of malware that are common in porn apps for Android include malicious clickers, banking Trojans, ransomware, rooting Trojans, premium SMS malware and fake porn subscriptions. The researchers also identified one more type, which, according to them, couldn't be attributed to any known group.
"A victim who has been compromised with an adult content-enabled malicious programme might think twice before reporting the incident, simply because they were trying to find porn content. This is one of the reasons why we see so many attacks with this malware," Roman Unuchek, a security expert at Kaspersky Lab, said in a statement.
Here is the distribution of users attacked by different kinds of porn malware in 2017:
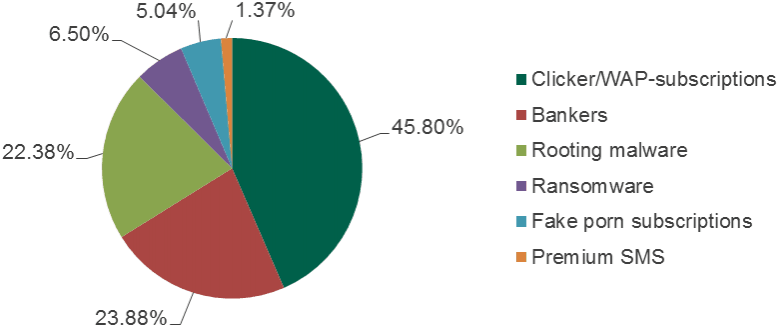
Clickers
The malicious clickers function by opening a web page and clicking on some buttons without user consent. They do it with mainly two goals: to click on advertising to receive money for a shown ad, but not showing it to the user; and to enable WAP-subscriptions, which leads to direct financial losses for the victims, especially in countries where pre-paid cellular plans are popular.
Banking Trojans and ransomware
Banking Trojans and ransomware have been using porn for their distribution. They have been operating mostly in disguise of a specific porn player, which compromises the security of the attacked device, instead of showing the expected content.

When it comes to banking Trojans, they use porn websites to distribute themselves, or just present themselves as a specific video player. Ransomware, on the other hand, often appears to be a legitimate porn app.
Rooting Trojans
Once installed, rooting Trojans that use porn topics for distribution can exploit vulnerabilities in Android devices and get access any data on the user's device. They can also silently install any applications and get direct remote access to infected devices.
"What is unusual about rooting malware is that such apps are often spread as part of legitimate applications. Cybercriminals just pick a porn app, add malicious code to it and distribute it as if it were legitimate," the researchers said.
SMS malware and fake subscriptions
These primitive Trojans are used only to send SMS or make calls asking victims to make payments to access a particular porn site, even though the content of the site is usually available without payment.
The mysterious 'Soceng'
The researchers have also identified an interesting Trojan that doesn't fall into any of the categories above: Trojan.AndroidOS.Soceng.f.
According to them, the malware is distributed mainly under the guise of games and programmes, but also sometimes under the guise of porn. The researchers noticed that the malware sample they were testing sent an SMS to the victim's entire phone book saying that they were hacked.
It also deleted all files from the memory card, and overlaid Facebook, Google talk, WhatsApp and MMS applications with its own window.
"We couldn't spot any attempts at financial gain through this malware, apparently its only purpose was to ruin the victims' digital life. Or it was a test attempt by another yet unknown cybercriminal operation," the researcher said.

















