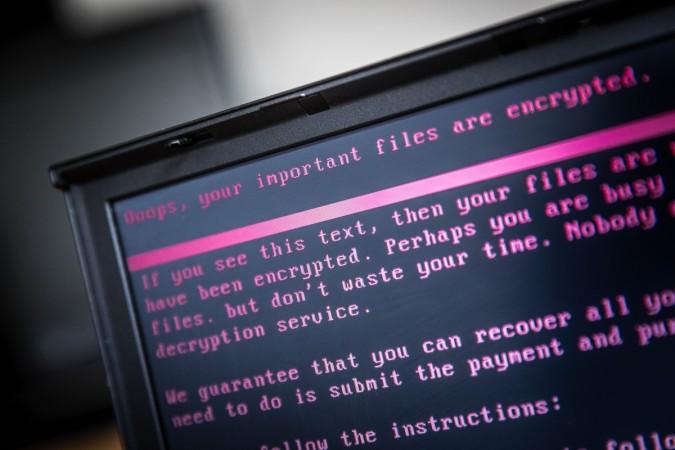
Weeks after a new strain of the notorious Petya ransomware created havoc by locking thousands of computers across the world, a cyber security firm has now given the victims some hope of getting their hijacked files back.
Positive Technologies, a Russian cyber security firm, claimed on Friday that its researchers have developed a method which can help decrypt files on computers infected by the NotPetya ransomware attack. According to the firm, it has successfully decrypted files damaged by NotPetya on one infected computer.
According to Dmitry Sklyarov, the head of reverse engineering at Positive Technologies, the creators of NotPetya made errors in their implementation of the Salsa20 encryption algorithm, which eventually led to "this latest breakthrough."
"Due to this error, half of the encryption key bytes were not used in any way. This reduction in key length from 256 to 128 bits, unfortunately, still does not leave any hope of decrypting data in a reasonable time. However, certain peculiarities of how the Salsa20 algorithm was applied allow recovering data, no key necessary," Sklyarov said in a blog post.
The potential solution, however, only works on systems on which NotPetya had secured administrator privileges, and encrypted the entire hard disk. Otherwise, the virus employs a different method of encryption, which isn't reversible without a private key.
"If NotPetya is unable to obtain administrator privileges when running, it performs AES encryption of user files only and the operating system continues to work. Unfortunately, recovering user files, in that case, requires knowing the private RSA key," Sklyarov said.
The Salsa20 algorithm activates when the ransomware secures admin rights. It damages the Master File Table (MFT) in an infected computer, making it impossible to recover the files.
Prof Alan Woodward, a security expert from the University of Surrey, told BBC that researchers at Positive Technologies might have discovered an unaffected portion of the MFT, which they thought could be recovered.
"If that is true, that would be a significant finding. It may actually allow people to recover the so-called boot disks, that contain the original operating system, which we were assuming you couldn't do." Woodward told BBC.
Last week, two separate reports from Comae Technologies and Kaspersky Lab said that NotPetya was not exactly a ransomware, but more of a disk wiper created to damage computers.
Ransomware tools generate a unique installation ID for each infected computer to store information and the decryption key for recovery. In the case of NotPetya, the installation ID is invalid as it is generated from random data, making the decryption process impossible, the reports said.

















