For nine months, South Korea has been the ground zero of the Magniber ransomware. But early this month, the malware started to expand its target spectrum to other East Asian nations, including China and Singapore.
Security researcher MalwareHunter first discovered the expansion of Magniber on July 5. The ransomware is targeting computers with Chinese and Malay language settings and has attacked China, Taiwan, Hong Kong, Macau, Singapore, Brunei, and Malaysia, so far.
Since Magniber identifies its potential victims by the language setting, files that get infected could possibly encompass those from other Asian countries, especially if the potential victims are using proxies with a Chinese or Malay IP.
Magniber is rooted from the Magnitude exploit kit, one of the longest-running browser exploitation toolkits that are still functional. Since its global distribution in 2013, the kit began to branch out to Magniber in October 2017 and zeroed in on South Korea. In April 2018, Magniber did come back as a better exploit, attacking more nations in Asia.
『the code of Magniber got updated to whitelist more languages. Now the list expanded, adding other Asian languages, such as Chinese (Macau, China, Singapore) and Malay (Malysia, Brunei).』?
— Autumn Good (@autumn_good_35) July 17, 2018
Magniber ransomware improves, expands within Asiahttps://t.co/VjNho5gabB pic.twitter.com/jekJV05LS5
In its analysis, cybersecurity firm Malwarebytes has detailed two significant changes in Magniber's binary and execution. The perpetrators have "improved" the ransomware since it was unleashed last year and its targeting
The ransomware carries out its operation with surgical precision, said researchers. "Criminals know exactly which countries they want to target, and they put their efforts to minimize noise and reduce collateral damage," wrote researchers at Malwarebytes, adding that its source code is now more refined.
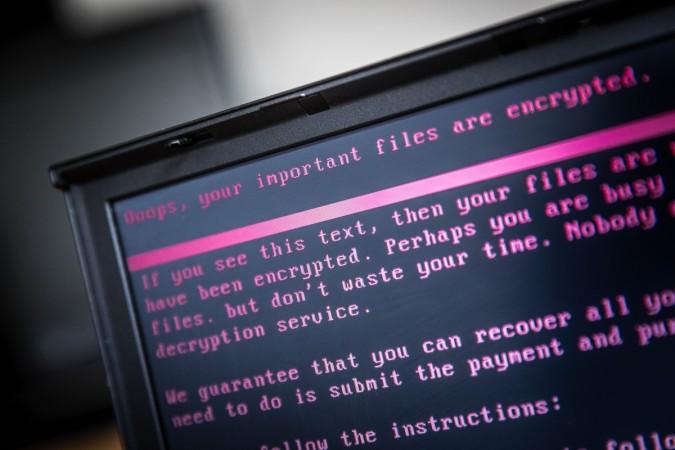
Like any other ransomware, Magniber operates by encrypting files in computers and they can only be recovered if the victim releases a payment, depending on the conditions of the attacker behind it. Infected files can be identified by the ".dyaaghemy" file extension at the end of the file name.
As of now, there is no solution in sight.

















