The emergence of new Internet of Everything 'surfaces' like connected cameras, cars, health and industrial automation devices are proving to be a great launch pad for the "hacking for hire" industry, says a new report from IT services major Wipro Ltd.
The first 'State of Cybersecurity Report 2017' launched on Thursday says that emerging IoT or Internet of Things devices come with low memory and processing footprint and usually accommodate very little security capabilities including patching.
"Such devices, once they are 'online' with an IP address, are easy prey for sophisticated hacking syndicates. These syndicates can develop custom malware to take control of IoT devices en masse and use them as a launchpad for cyber attacks," the cyber security report, which surveyed CISOs (Chief Information Service Officers) across 139 organisations spread across 11 countries, said.
The study said a majority of security products are themselves vulnerable to exploitation and CISOs will be required to keep track of vulnerabilities in the security products themselves.
The responsibility for governance of data privacy is still highly centralised, lying with either the CIO, CISO or CPO for 71 percent of organizations, the report said. Managing privileged access to data was ranked as the highest control amongst data security controls.
Cyber insurance expensive
"Cyber security is becoming a top priority for businesses. It has become very critical to identify risks near real-time and empower stakeholders to take actions and decisions based on priority. The report highlights crucial findings on attacks, vulnerabilities and cyber defence that are useful for teams across cybersecurity strategy, operations and risk management," said Sheetal Mehta, Vice-President and Global Head, Cybersecurity & Risk Services, Wipro Limited.
Cyber Insurance might turn out to be an alternative risk transfer mechanism for IoT providers if they cannot address the security vulnerabilities and risks inherent in these platforms. The size of DDoS (Distributed Denial of Service) attacks has reached a whopping 990 Gbps using 150,000 compromised public IoT-enabled CCTV cameras, Wipro's cybersecurity report points out.
Trojan.Gen.2 was the most popular Trojan of 2016. Trojans, followed by worms and viruses, occupy the top three positions among various types of malware detected in 2016. The number of stolen records through malware attacks rose 53.6 percent in 2016. 'Angler' was the most observed exploit kit used by cyber criminals, followed by RIG and Nuclear.
Fifty-eight percent of respondents to the security survey done by Wipro experienced some form of DDoS attacks last year. Wipro analysed thousands of attempted security attacks and incidents captured in Wipro's Cyber Defence Centres during 2016.
The report notes that one of the biggest challenges for enterprises to adopt cloud-based platforms has been loss of control over data and compliance with regulatory processes. Once the data moves out of the enterprise periphery to the cloud environment, there is a loss of control particularly over what the privileged users of the cloud services provider can do with the data. The concept of BYOK (Bring Your Own Key) needs to be increasingly adopted within the enterprise, the report said.
Bring your own encryption (BYOE), also called bring your own key (BYOK), refers to a cloud computing security model to help cloud service customers to use their own encryption software and manage their own encryption keys.
The report noted that BYOK might be a game changer for cloud adoption by giving compliance and control to enterprises over their data wherein the enterprises could hold on to their keys and an agent housed with the cloud provider could provide the real-time encryption and decryption capability.
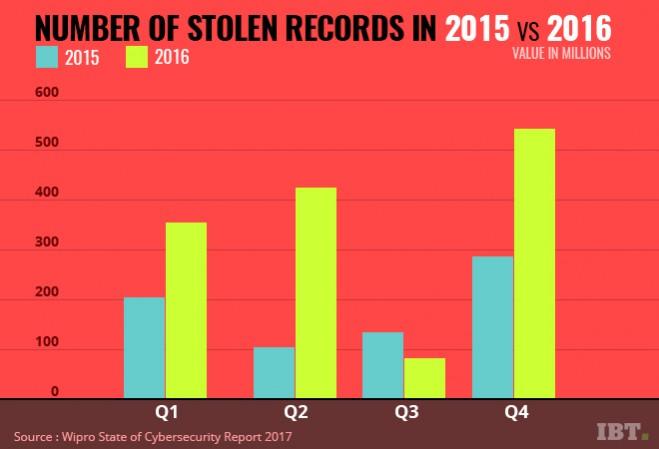
Stolen records on the rise
The report noted that 2016 saw unprecedented cyber attacks across different commercial sectors and geographical locations.
"However, what probably catapulted cybersecurity to the limelight for the first time in the political arena was the recently concluded US presidential election. The year has seen it all: 53.6 percent increase in data records stolen across the globe for reported breaches, unprecedented DDoS (Distributed Denial of Service) attacks peaking at a phenomenal 990 GBPS, newer versions of highly evolved malware families and evolving regulations that enterprises need to be bound by," the report said, noting that the defensive tactics currently employed haven't kept pace with the sophistication of the attacks.
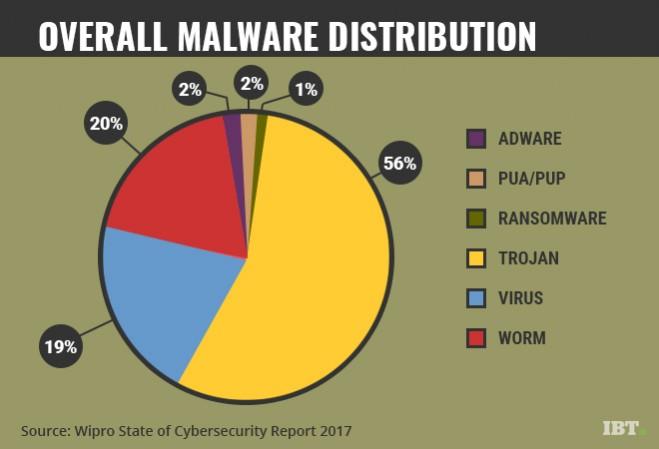
Fifty-six percent of the breaches reported had user credentials (passwords) as part of the types of data stolen, implying that further damage could be perpetrated using the stolen data, according to Wipro's Cyber Defence Center (CDC) data analysis.
Viruses and 'worms' accounted for 19 percent and 20 percent respectively. Other types of malware threat categories like PUA, adware, and ransomware, together, though accounting for only 4 percent of attacks, could often cause significant damage in future attacks, the report warned.














