
In December 2016, some part of Ukraine's capital, Kiev, suffered a power outage for about an hour due to a cyber-attack on the country's power grid. Researchers from two cyber security firms now have said that they have finally detected the malware, which likely caused the blackout. What's even more concerning is the fact that hackers can easily modify the malicious software to harm critical infrastructure operations globally.
Identified as "Industroyer" or "Crash Override", the malware can be used by its creators to launch more attacks while there is also threat from its copycat versions as well, according to ESET, a Slovakian anti-virus software maker, and Dragos Inc, a U.S. critical infrastructure security firm. The two firms, meanwhile, have also issued private alerts to governments and infrastructure operators to help them better defend against the malware.
Simple modifications turn Industroyer more lethal
Researchers at ESET, who termed the malware as Industroyer, said that it can directly control electricity substation switches and circuit breakers. To make that happen, the malware exploits industrial communication protocols used worldwide in power supply infrastructure, transportation control systems and other critical infrastructures including water and gas.
The malware, which is very easy to re-purpose and use against targets, can have various infrastructure impacts, ranging from simply turning off power distribution channels to more serious damage to equipment. It contains certain features that are designed to enable it to remain unnoticed.
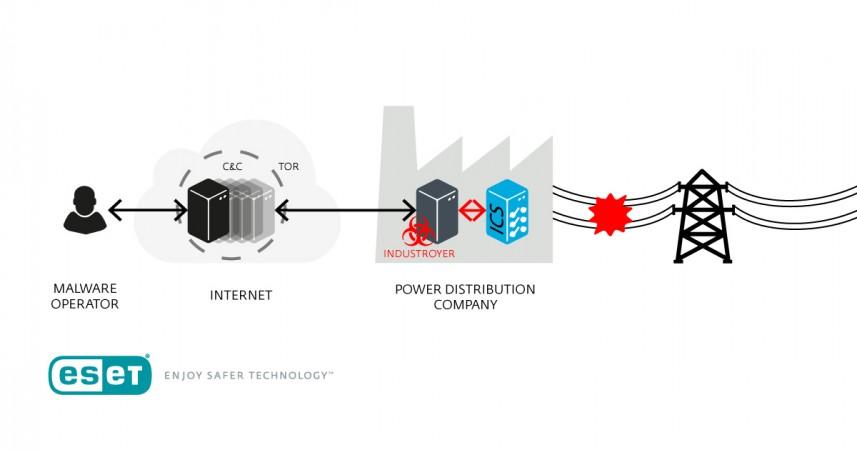
According to Dragos founder Robert M. Lee, the malware is capable of attacking power systems across Europe while it can also be used against the US "with small modifications". Lee, however, also said that the malware can cause an outage for a few days in portions of a nation's grid, but it cannot bring down the entire power grid of a country, Reuters reported.
Meanwhile, the U.S. Department of Homeland Security said it was investigating the malware, though there was no evidence of the malware infecting the country's critical infrastructure. The agency, however, posted technical indicators on its website to help firms better detect potential cyber-attacks caused by the malware.
Dragos, which called the malware Crash Override, said that hackers have not used all of its functionalities and modules, and the attack on Ukraine's power grid in 2016 was more of a proof of concept attack, rather than a full demonstration of the malware's capabilities.
How does it work?
"The modules in CRASHOVERRIDE are leveraged to open circuit breakers on RTUs [remote terminal units] and force them into an infinite loop keeping the circuit breakers open even if grid operators attempt to shut them. This is what causes the impact of de-energising the substations," Dragos said in a blog post, adding that grid operators can alleviate this issue by going back to manual operations.
"Industroyer's ability to persist in the system and to directly interfere with the operation of industrial hardware makes it the most dangerous malware threat to industrial control systems since the infamous Stuxnet, which successfully attacked Iran's nuclear programme and was discovered in 2010," Anton Cherepanov, senior malware researcher at ESET said in a statement.
Many security researchers believe that Stuxnet was used by the U.S. and Israel to cause substantial damage to Iran's nuclear programme. Stuxnet functioned by targeting machines using the Microsoft Windows operating system and networks, and reportedly compromised Iranian programmable logic controllers.

















