![[Representational Image] Steps to prevent hacking In Picture: Laptop hacking, US Homeland security, FBI, GRIZZLY STEPPE, US elections 2016 rigging](https://data1.ibtimes.co.in/en/full/606868/hacking.jpg?h=450&l=50&t=40)
After reports emerged that Russian hackers might have been involved in the rigging of the recently concluded US 2016 elections, the government-run Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) conducted a joint-probe to ascertain the real damage.
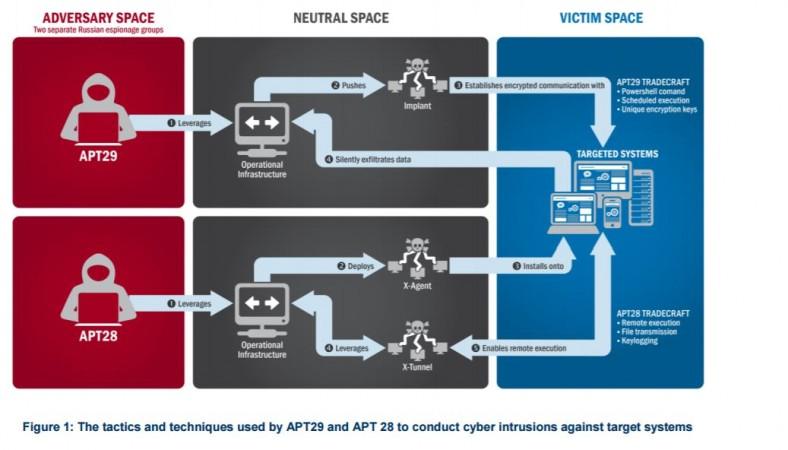
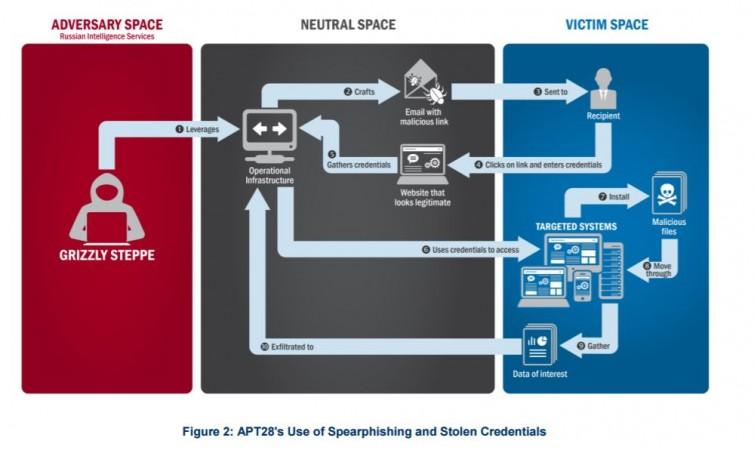
After thorough inquiry, they have released the Joint Analysis Report (JAP) confirming Russian Military and its civilian intelligence services guilty of malicious cyber activity dubbed as the "GRIZZLY STEPPE" in US Elections 2016 results and also hacking of a range of U.S. government, political and private sector entities, as well.
Also read: Obama says US will retaliate against Russian hacking as RNC claims it foiled infiltration
The JAP report has cautioned security companies and private sector owners and operators to look back within their network traffic for signs of the malicious activity and come up with a slew of cyber security measures to thwart future threats.
Here are the steps organisation has to implement to help prevent and mitigate against attacks:
1. Patch applications and operating systems – Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker. Use best practices when updating software and patches by only downloading updates from authenticated vendor sites.
2. Application whitelisting – Company's computer admin has to list all the trust worthy application software and routinely monitor unauthorised programs from running on systems. The purpose is primarily to protect computers and networks from hacking.
3. Restrict administrative privileges – Threat actors are increasingly focused on gaining control of legitimate credentials, especially those associated with highly privileged accounts. Reduce privileges to only those needed for a user's duties. Separate administrators into privilege tiers with limited access to other tiers.
4. Network Segmentation and Segregation into Security Zones – Segment networks into logical enclaves and restrict direct host-to-host communications paths. This helps protect sensitive information and critical services and limits damage from network perimeter breaches.
5. Input validation – Input validation is a method of sanitising untrusted user input provided by users of a web application, and may prevent many types of web application security flaws, such as SQLi, XSS, and command injection.
6. File Reputation – Tune Anti-Virus file reputation systems to the most aggressive setting possible; some products can limit execution to only the highest reputation files, stopping a wide range of untrustworthy code from gaining control.
7. Understanding firewalls – When anyone or anything can access your network at any time, your network is more susceptible to being attacked. Firewalls can be configured to block data from certain locations (IP whitelisting) or applications while allowing relevant and necessary data through.
Cybersecurity best practices defined by DHS's National Cybersecurity and Communications Integration Center (NCCIC):
1. Backups- Always backup all critical information. If possible try to store backups offline tested and routinely conduct mock drill to test the company's ability to revert to backups during an incident.
2. Risk Analysis- It is a good practice to do risk analysis of oraganisation's Firewall so that the IT staff is better prepared for untoward incidents.
3. Staff Training- IT staff have to be routinely educated about recent developments on cyber scams and also best methods to thwart and recover in the event of cyber attacks.
4. Vulnerability Scanning & Patching- IT admins of the company have to perform regular scans of the company's network and systems and immediately perform necessary patching of known system if they find any vulnerabilities.
5. Application Whitelisting- System admins and software programmers of the company have to practice running only authorised application on their systems.
6. Incident Response- Make a practice of doing mock drill to hack into their our own systems to test the security of the company's systems and the ability to so that you are better prepared to defend against attacks.









!['Had denied Housefull franchise as they wanted me to wear a bikini': Tia Bajpai on turning down bold scripts [Exclusive]](https://data1.ibtimes.co.in/en/full/806605/had-denied-housefull-franchise-they-wanted-me-wear-bikini-tia-bajpai-turning-down-bold.png?w=220&h=138)



