Just when the cyber world beginning to recuperate from the latest ransomware attacks such as the deadly WannaCry and Petya, old malware such as Mamba and Locky, which were dormant since last year, are said to make a return for another bout of attacks, say the new reports.
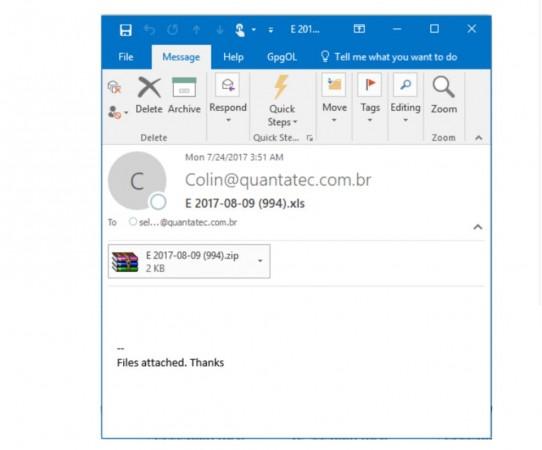
Between August 9 and 12 (lasting 72 hours), ransomware called IKARUSdilapidated landed in tens of thousands of inboxes with emails containing malicious dropper file attachments, reported Comodo Threat Intelligence Lab.
Also read: Google's Android team track, kill deadly Lipizzan malware in record time
It has come to light that IKARUSdilapidated might be a variant of Locky malware, as it has the same modus operandi. It converts encrypted filenames to a unique 16-letter and number combination with the .locky file extension.
Locky malware:
Locky malware made its first appearance in the US last year, where it attacked two prominent infirmaries in Los Angeles-- Hollywood Presbyterian Medical Center and Methodist Hospital, locking away the medical records of the patients. The former reportedly paid $17,000 (€14,483/Rs. 10,09,465) ransom in Bitcoins to hackers.
It was revealed that an unsuspecting employee received spam and launched the file attachment that in turn downloaded ransomware from the criminals' server, letting Locky into the network.
The Trojan quickly copied all the data on the device, encrypted it and deleted originals. Simultaneously Locky started to quickly infiltrate into the hospital's corporate network, which could be stopped only by turning off all of the PCs, Kaspersky reported.
Later hackers modified their tactics and switched to zip-archives with Java scripts, which also downloaded the Trojan from criminals' servers and launched it. The majority of malicious letters were in English, but there were also emails, written in two languages simultaneously.
What makes Locky malware more deadly than any other malware is that it is capable of understanding the sensitivity of the hacked files and set an individual price-tag for particular data and earn high-value ransom in quick time.
So far, Locky malware is said to have extorted more than $7.8 million in payments from victims.
According to Kaspersky Security Network, Locky is mostly active in Germany, France, Kuwait, India, South Africa, USA, Italy, Spain and Mexico.
Mamba malware:
Besides Locky, Mamba is also said to be making a comeback. It is developed by the notorious group with same names. They develop their own encryptor malware, based on the open source software DiskCryptor, which is also known as Full Disk Encryption (FDE) tool.
Once the Mamba group gains an entry to the network, they install the encryptor across it, using a legal utility for Windows remote control. This approach makes the actions less suspicious for security officers of the targeted organisation.
With FDE tool, Mamba malware encrypts everything in computer's Hard Disk Drive (HDD) and lock it with a password. When the victim switches the PC, it will ask for the ransom (in Bitcoin) for the access key to use it. If the information in the system is very sensitive, he/she has no choice but to succumb to demand and transfer the money to the hackers.
Kaspersky Lab's researchers have encountered cases where the ransom amounted up to one Bitcoin (around $1,000 to the end of March 2017) per one endpoint decryption.
Here's how to protect your PCs from malware:
- Always keep your PCs updated with latest firmware; most software companies including Microsoft and Apple usually send software updates regularly in terms of weekly or monthly
- Make sure to use premium anti-virus software, which also provides malware protection and internet security
- Never ever open email sent from unknown senders
- Never ever install plugins (for browsers) and application softwares on the PCs from un-familiar publishers
Also read: Here's US Homeland Security and FBI-approved steps to improve cybersecurity
Follow us @IBTimesIN_Tech on Twitter for latest news on cyber security and more.

















