With Cryptocurrency value on the rise, several cyber criminals have devised methods to dupe unwitting internet users and now, hackers have reportedly infected Facebook Messenger with malicious code for remote cryptocurrency mining.
Trend Micro's intelligence team has discovered a nefarious cryptocurrency-mining bot dubbed as Digmine, which is spreading through Facebook Messenger. First discovered in South Korea, it is steadily spreading across the world, which includes Vietnam, Azerbaijan, Ukraine, Vietnam, Philippines, Thailand, and Venezuela.
As per the report, though it works across different platforms, Digmine only affects desktop/web browser (Chrome) version. Thank fully, if the file is opened on other platforms (e.g., mobile), the malware will not work as intended.
How Digmine infect computers?
Digmine malware is sent to victims posing as a harmless video file, but in reality, it is an AutoIt executable script.
If the user's Facebook account is set to log in automatically, Digmine will manipulate Facebook Messenger in order to send a link to the file to the account's friends and spread, Trend Micro claims.
As of now, the abuse of Facebook's auto login feature on Chrome browser is limited to propagation of Digmine for now, but it won't be a surprise if the cyber criminals highjack the whole social media account in near future.
Digmine is capable of getting updated with newer codes, as it can access from remote command-and-control (C&C) server.
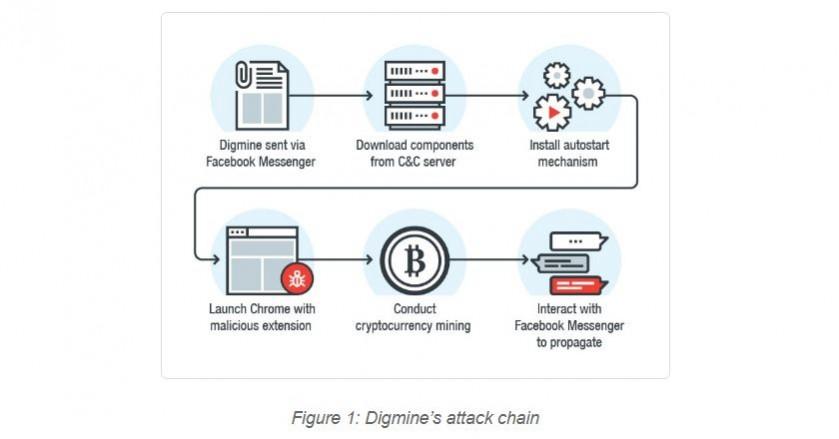
A known modus operandi of Digmine is to spread to as many systems as possible and with increased hash rate, more income they get.
[Note: Hash rate is the speed at which a computer is completing an operation in the Bitcoin code. A higher hash rate is better when mining as it increases your opportunity of finding the next block and receiving the reward.]
Hackers are particularly mining Monero, alternate Bitcoins digital currency, which once gained, is said to be secure, private and untraceable.
Monero is a Proof of Work cryptocurrency that can be mined with computational power from a CPU or GPU. As per Cryptocompare, mining metrics are calculated based on a network hash rate of 496 MH/s and using a XMR - USD exchange rate of 1 XMR = $ 341.06. These figures vary based on the total network hash rate and on the XMR to USD conversion rate. Block reward is fixed at 5.77378715772 XMR.
Indicators of Digmine malware Compromise (IoCs):
Hash detected as TROJ_DIGMINEIN.A (SHA256);
- beb7274d78c63aa44515fe6bbfd324f49ec2cc0b8650aeb2d6c8ab61a0ae9f1d
Hash detected as BREX_DIGMINEEX.A (SHA256):
- 5a5b8551a82c57b683f9bd8ba49aefeab3d7c9d299a2d2cb446816cd15d3b3e9
Hash detected as TROJ_DIGMINE.A (SHA256):
- f7e0398ae1f5a2f48055cf712b08972a1b6eb14579333bf038d37ed862c55909
C&C servers related to Digmine (including subdomains):
- vijus[.]bid
- ozivu[.]bid
- thisdayfunnyday[.]space
- thisaworkstation[.]space
- mybigthink[.]space
- mokuz[.]bid
- pabus[.]bid
- yezav[.]bid
- bigih[.]bid
- taraz[.]bid
- megu[.]info
Here's how to protect your PCs from Digmine malware and ransomware:
- Always keep your PCs updated with the latest firmware; most software companies including Microsoft and Apple usually send software updates regularly in terms of weekly or monthly and make sure to update them immediately
- Make sure to use premium Anti-virus software, which also provides malware protection and Internet security
- Never open email sent from unknown senders
- Disable ActiveX content in Microsoft Office applications such as Word, Excel, etc.
- Disable Remote Desktop Connections, employ least-privileged accounts. Limit users who can log in using Remote Desktop, set an account lockout policy. Ensure proper RDP logging and configurations
- Never install plugins (for browsers) and application software on the PCs from un-familiar publishers
- System administrators in corporate companies should establish a Sender Policy Framework (SPF) for their domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.









