Coronavirus has created a panic among people and ignited a sense of responsibility to maintain personal hygiene and social distancing. The growing number of Covid-19 cases and deaths is closely monitored by people, for which reason there are a lot of apps and services offering an easy way to get live updates. But slight negligence can result in falling prey to a treacherous ransomware attack.
The rise in malware-ridden coronavirus apps has forced Google and Apple to take serious action in removing such malicious apps. But there is no stopping cybercriminals, who are finding new ways to trick Android and iOS marketplaces to get fund their ulterior motives.
Researchers at the DomainTools discovered a malicious app that is disguised as a coronavirus tracker, but it is to be avoided at all costs. Here's how the app works in reality.
CovidLock: Ransomware in disguise
It all starts with a malicious coronavirus tracker website, where users are prompted to install and Android app in order to receive tracking and statistical information about Covid-19. What lures users to this app is the promise of notifying its users when a "coronavirus patient is near you."

Since it is advised to stay away from coronavirus patients to avoid getting infected, this app's USP of alerting you when there's an infected individual nearby is likely to fetch a lot of downloads. For that, the app seeks various kinds of permissions, which grants full access to the device. If the user doesn't suspect this behaviour, the worst is to follow.
Ransom demand
When the malicious CovidLock app has all the access, it then locks the users' smartphone and demands a ransom of $100 in Bitcoin currency within 48 hours. Failing to comply, the app threatens to delete all data on the phone, including contacts, photos, videos and the entire content.
If users have any embarrassing or personal content on social media, things get seriously scary. The app threatens to leak users' social media accounts publicly. To scare users, the app also says, "Your GPS is watched and your location is known, if you try anything stupid your phone will be automatically erased."
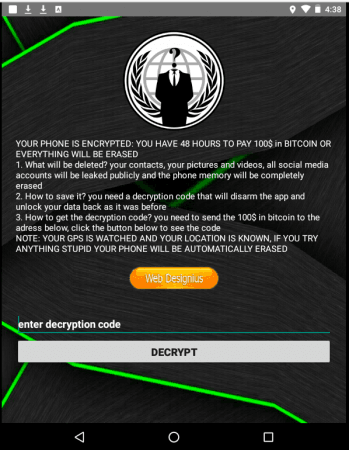
Since the app uses the phone's lock to initiate a lockdown, phones without a lock are also vulnerable, researchers say.
What should users do?
If any user is affected by CovidLock ransomware, DomainTools has an instant fix. After reverse-engineering CovidLock's decryption key, the researchers have published a master key to bypass the ransomware screen. Affected users can enter: 4865083501 in the box provided on the phone screen to regain access to all the content. And, no you don't have to pay $100 ransom.
As for those who haven't been affected, always rely on trusted sources from government, research institutes and media publications. If anything looks suspicious, do not click on it. Besides ransomware, users can be affected by malware or be a victim of a phishing attack.
Always verify the source of an app, carefully grant necessary permissions and avoid downloading apps from third-party sources.















