Hackers are constantly on the lookout for new ways to exploit vulnerabilities. Getting access to smartphones via malicious apps isn't a new practice for cybercriminals. But it's alarming to see how hackers can still find a way into users' phones despite enhanced security. A new report sheds light on three such apps that grant hackers access to users' Android phones and here's how you can prevent being hacked.
Trend Micro, a cybersecurity research firm, discovered three malicious apps on Google Play Store, the go-to app marketplace for billions of Android users. The apps, identified as Camero, FileCryptManager and CallCam disguised as photography and file manager tools, serve as a gateway for hackers to steal information without users ever knowing.
According to the researchers, the malicious apps belong to a hacker group called "SideWinder," which were reportedly behind the attack on military entities' Windows machines. The ill-intended apps no longer appear on Play Store, but continue to pose a risk to those who still have them on the phones. The apps are said to be active since March last year, researchers speculated.

What is the risk?
According to the report, the malicious apps infect the target device and hide the icon so users cannot remove it. The apps run in the background to collect data stored on the device. Furthermore, the stolen data is encrypted using RSA and AES encryption and sent to the attacker's C&C server.
The researchers found the three apps to be stealing wide range of information, including location, battery status, files on device, list of apps installed on phone, device information, sensor information, camera information, screenshots, account details, Wi-Fi information and data stored by popular apps like Facebook, Gmail, Chrome, WeChat, Outlook, Twitter and Yahoo Mail.
How Android devices are infected?
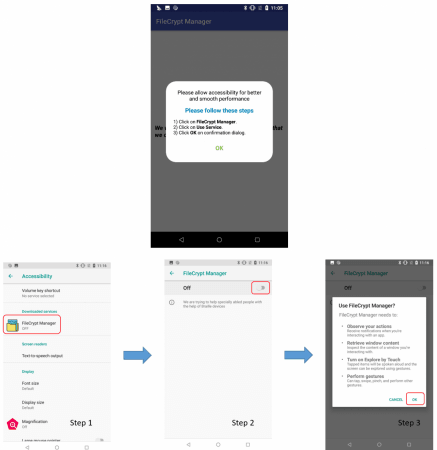
The hacker group deploys the attack in two stages. First, it downloads the DEX file from the attacker's C&C service and then downloads an APK, which is installed after the device is infected and hackers gain access. The entire process happens in stealth and hackers use techniques like "obfuscation, data encryption, and invoking dynamic code," researchers noted.
Using these malicious apps, hackers can also root the device to gain "accessibility permission" on the targeted device. This gives hackers the ability to secretly install malware or any apps without the user's knowledge.
What should users do?

Android smartphone users must go through their apps on the phone. To do so, go to Settings > Apps to properly check the list as malicious apps often hide icons from home screen. If you find any of the three malicious apps, Camero, FileCryptManager and CallCam, immediately uninstall them.
As a measure of precaution, uninstall any apps that you do not recognise or use anymore.














